Voice over Internet Protocol (VoIP) systems are essential for modern communication, providing flexibility and cost savings. However, these systems also come with significant security risks. Cybercriminals are continually developing new techniques to attack VoIP systems.
Common threats include eavesdropping, data interception, and denial of service (DoS) attacks.These security risks can lead to the exposure of sensitive information and disrupt business operations. It is crucial to implement robust security measures, whether you use a VoIP service provider or manage your own system.
In this blog, we will discuss the most common cyber threats facing VoIP systems today. We’ll also offer practical, actionable steps to help you protect your communications from these cyber threats. You can keep your data and business operations secure by following these guidelines.
Understanding VoIP Vulnerabilities
- Unencrypted Data Transmission: VoIP calls often travel over the internet without encryption, making them vulnerable to interception. This means sensitive conversations can be eavesdropped on by unauthorized parties.
- SIP Trunking Vulnerabilities: SIP trunking connects VoIP systems to the public switched telephone network (PSTN). If not secured properly, this connection can be exploited by attackers, who might intercept or manipulate communication signals.
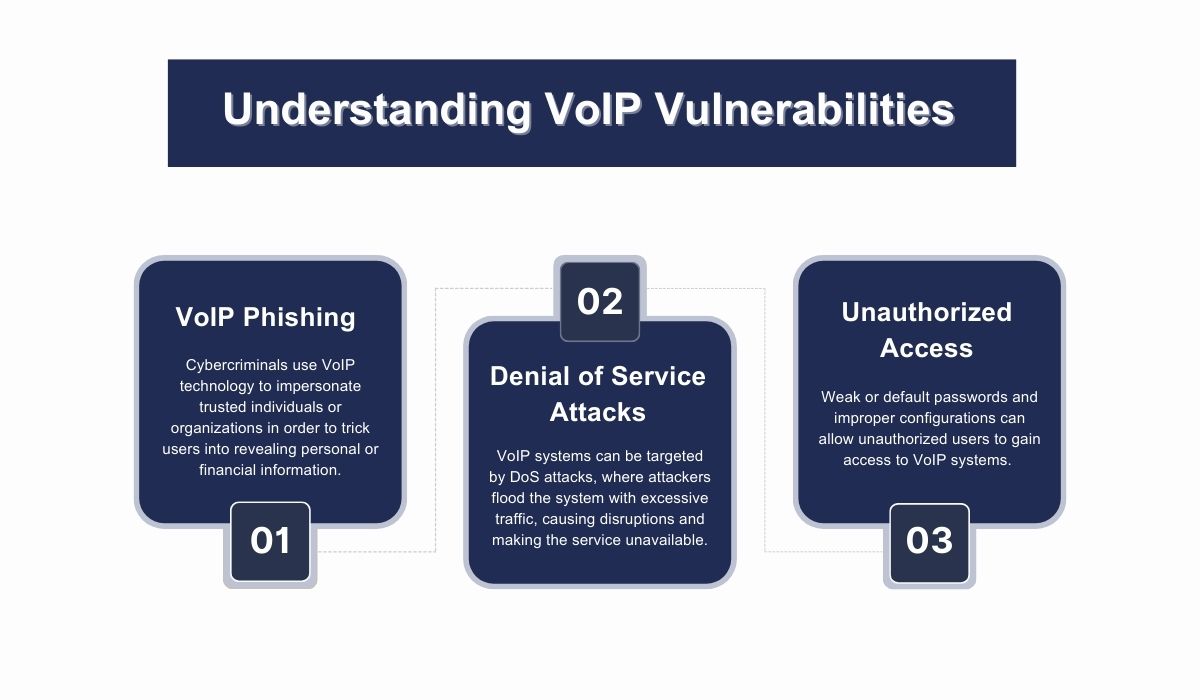
- VoIP Phishing (Vishing): Cybercriminals use VoIP technology to impersonate trusted individuals or organizations in order to trick users into revealing personal or financial information. This practice, known as vishing, can lead to identity theft and financial loss.
- Denial of Service (DoS) Attacks: VoIP systems can be targeted by DoS attacks, where attackers flood the system with excessive traffic, causing disruptions and making the service unavailable. This can impact business operations and customer communication.
- Unauthorized Access: Weak or default passwords and improper configurations can allow unauthorized users to gain access to VoIP systems. Once inside, they can cause data breaches or misuse the system for fraudulent activities.
- Call Interception and Spoofing: Without proper security measures, VoIP calls can be intercepted or spoofed, allowing attackers to listen in on conversations or impersonate legitimate users, leading to potential misinformation or fraud.
- Inadequate Authentication: VoIP systems with insufficient authentication methods are vulnerable to unauthorized access. Attackers may exploit this weakness to gain control over the system, resulting in security breaches and system misuse.
The Importance of Securing VoIP Systems
- Protecting Sensitive Information: VoIP systems often handle confidential business communications, including personal data and financial details. Securing these systems ensures that sensitive information is not intercepted or accessed by unauthorized parties, safeguarding against data breaches and identity theft.
- Maintaining Business Continuity: Unsecured VoIP systems are vulnerable to disruptions from cyberattacks, such as Denial of Service (DoS) attacks. By securing your VoIP system, you minimize the risk of service outages, ensuring continuous and reliable communication essential for business operations. Reliable VoIP solution providers can help maintain this continuity.
- Preventing Financial Loss: Cybercriminals can exploit vulnerabilities in VoIP systems to commit fraud or steal financial information. Effective security measures help prevent financial loss by protecting against phishing (vishing) attacks and unauthorized transactions.
- Ensuring Compliance: Many industries are subject to regulatory requirements that mandate the protection of communication data. Securing your VoIP system helps ensure compliance with data protection laws and industry regulations, avoiding potential legal penalties.
- Safeguarding Against Unauthorized Access: VoIP systems with weak security can be exploited for unauthorized access, leading to potential misuse of the system and confidential information. Strong security practices prevent unauthorized users from gaining control and compromising the system.
- Enhancing Customer Trust: Securing your VoIP system demonstrates a commitment to protecting customer data and maintaining privacy. This builds trust with clients and partners, enhancing your organization’s reputation and credibility.
- Protecting Against Spoofing and Interception: Without adequate security, VoIP calls can be intercepted or spoofed, allowing attackers to impersonate legitimate users or listen to private conversations. Securing your system ensures that communications remain confidential and authentic. Trusted VoIP solution providers can help prevent these security issues.
Best Practices for Securing Your VoIP System
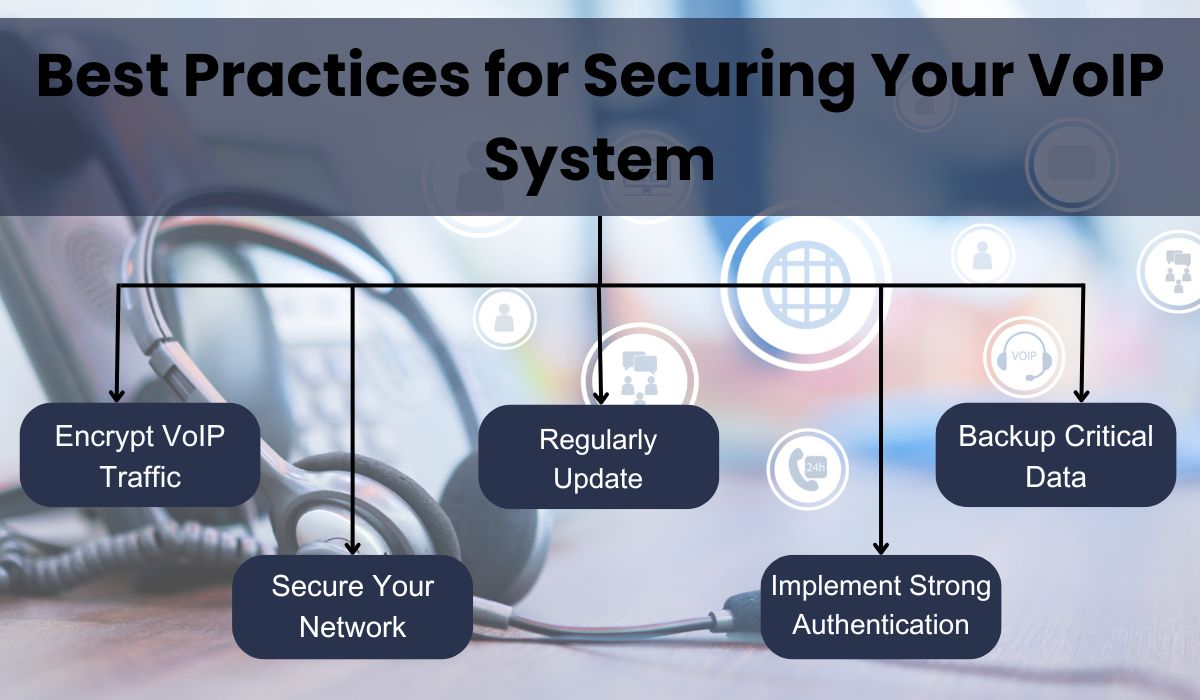
- Implement Strong Authentication: Use complex, unique passwords for all VoIP accounts and administrative interfaces. Enable two-factor authentication (2FA) to add an extra layer of security, ensuring only authorized users can access the system.
- Encrypt VoIP Traffic: Apply encryption protocols such as Secure Real-time Transport Protocol (SRTP) and Transport Layer Security (TLS) to protect voice and signaling data from being intercepted or eavesdropped on.
- Secure Your Network: Deploy firewalls to block unauthorized access and intrusion detection systems (IDS) to monitor for suspicious activity. Isolate VoIP traffic on a separate network or VLAN to reduce exposure to potential threats. Consult with VoIP system providers for effective network security configurations.
- Regularly Update and Patch Systems: Keep all VoIP-related software, including firmware and applications, up-to-date with the latest security patches.
- Configure Secure VoIP Settings: Disable unused features and services that may present security risks. Use secure methods for SIP trunking and avoid exposing SIP signaling to the public internet.
- Educate and Train Employees: Provide training on recognizing and avoiding VoIP-specific threats like phishing (vishing) and social engineering. Regularly update training materials to address new and evolving threats.
- Monitor and Log Activity: Implement monitoring tools to track VoIP system performance and detect unusual activities. Maintain detailed logs of all VoIP interactions and review them periodically for signs of unauthorized access or anomalies.
- Backup Critical Data: Regularly back up VoIP system configurations and data. Test backup procedures to ensure quick and effective restoration in case of an attack or system failure.
Conclusion
Securing your VoIP system is essential to protect sensitive data, maintain business continuity, and safeguard against financial and reputational damage. By implementing robust security measures and following best practices, you can effectively mitigate the risks associated with VoIP vulnerabilities.
For expert assistance in securing your VoIP system and ensuring your communications are protected, consider reaching out to ICS. Our team of experienced VoIP solution providers is here to help you enhance your security posture and keep your business safe from cyber threats. Contact us today to learn more.